How to Block SYN Attacks
What is a SYN flood attack? How to Block SYN DDoS?
In order to understand how to block SYN attacks, it is first necessary to understand what it is. We’ll start with the basics:
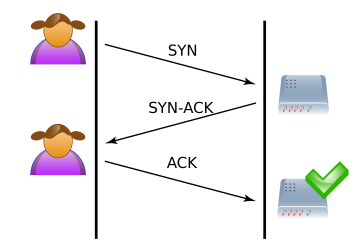
1. The client initiates a connection with the server by sending a SYN (synchronise) packet.
2. The server responds with SYN-ACK to the client, indicating that it has received the request.
3. The connection is established when the client answers with an ACK. This is referred known as the TCP three-way handshake.
Protection from SYN flood attacks
1. On servers that aren’t correctly configured to handle SYN floods, they can trigger serious denial of service (DoS) assaults.
2. The first line of defense is usually proper firewall filtering policies, however the Linux kernel can also be hardened against these types of assaults.
3. SYN floods, which aim to overload a specific service (such as http), are effective with this type of hardening, unlike SYN floods, which attempt to saturate the server’s network connection and which must be protected by a firewall.
SYN flood protection with firewall rules
Firewall rules can be set up on the software level to allow or disallow protocols, ports, or IP addresses. For example, in the event of a targeted attack originating from a small number of unusual IP addresses, a simple rule could be sufficient to filter out any incoming traffic from such attackers.
- Protection using iptables
Iptables is the default firewall for Linux systems. Harden your firewall by blocking all incoming traffic except that which your server absolutely requires. It’s simple to get rid of attack from a single host without IP spoofing:
# iptables -A INPUT -p tcp -m state –state NEW -m recent –update –seconds 20 –hitcount 20 -j DROP
# iptables -A INPUT -p tcp -m state –state NEW -m recent –set -j ACCEPT
This limits the SYN requests from an IP to 20 per 20 seconds. Also, such rules shouldn’t be used on regular basis to avoid block to ligitimate vistitors.
Run the following command through SSH to check for SYN packets on your Linux server:
# netstat -anp | grep SYN -c
- Protection using CSF (ConfigServer Firewall)
It is a configuration script designed to improve server security while providing an advanced, user-friendly interface for configuring firewall settings. CSF configures your server’s firewall to restrict public access to services and only allow specific connections, such as FTP, email, and website loading.
LFD is a service included with CSF which monitors user behavior for unusually high login failures, which are prevalent during brute force attempts. IP will be temporarily barred if large number of failed login attempts are seen. These IP blocks will automatically expire, however they can be removed manually.
- Settings to tweak within CSF to block SYN attacks:
1. Check for “Port Flood Settings” in CSF configuration file.
2. Now you will be able to see the parameters “SYNFLOOD_BURST” & “SYNFLOOD_RATE”.
3. “SYNFLOOD_RATE” is the number of SYN packets to accept per IP, per second
4. “SYNFLOOD_BURST”, here if the IP hits the limit, it will get blocked.
Once the parameters are set, we need to restart the CSF and LFD service for the changes to come into effect. Congratulations, you have successfully set up your server to block SYN attacks!
Are you facing an attack on your website currently? Looking for DDoS protected hosting? Contact the hosting experts at RackNerd! Please feel free to e-mail us at sales@racknerd.com for assistance.
